Cybersecurity researchers have disclosed particulars of a now-patched safety flaw within the Amazon EC2 Easy Methods Supervisor (SSM) Agent that, if efficiently exploited, might allow an attacker to attain privilege escalation and code execution.
The vulnerability might allow an attacker to create directories in unintended places on the filesystem, execute arbitrary scripts with root privileges, and sure escalate privileges or carry out malicious actions by writing information to delicate areas of the system, Cymulate said in a report shared with The Hacker Information.
Amazon SSM Agent is a element of Amazon Net Providers (AWS) that allows directors to remotely handle, configure, and execute instructions on EC2 cases and on-premises servers.
The software program processes instructions and duties outlined in SSM Documents, which may embody a number of plugins, every of which is chargeable for finishing up particular duties, akin to operating shell scripts or automating deployment or configuration-related actions.
What’s extra, the SSM Agent dynamically creates directories and information primarily based on the plugin specs, sometimes counting on plugin IDs as a part of the listing construction. This additionally introduces a safety threat in that improper validation of those plugin IDs can result in potential vulnerabilities.
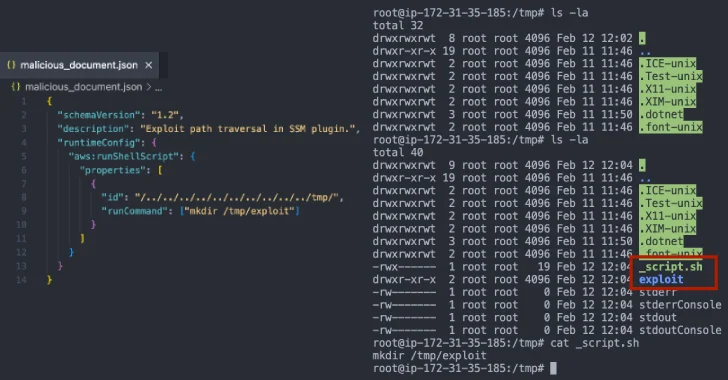
The invention by Cymulate is a path traversal flaw arising on account of improper validation of plugin IDs, which might enable attackers to govern the filesystem and execute arbitrary code with elevated privileges. The difficulty is rooted in a perform named “ValidatePluginId” inside pluginutil.go.
“This perform fails to correctly sanitize enter, permitting attackers to produce malicious plugin IDs containing path traversal sequences (e.g., ../),” safety researcher Elad Beber stated.
On account of this flaw, an attacker might basically furnish a specifically crafted plugin ID when creating an SSM doc (e.g., ../../../../../../malicious_directory) to execute arbitrary instructions or scripts on the underlying file system, paving the way in which for privilege escalation and different post-exploitation actions.
Following accountable disclosure on February 12, 2025, the vulnerability was addressed on March 5, 2025, with the discharge of Amazon SSM Agent version 3.3.1957.0.
“Add and use BuildSafePath methodology to forestall path traversal within the orchestration listing,” in line with launch notes shared by the challenge maintainers on GitHub.
Source link