No less than 4 completely different menace actors have been recognized as concerned in an up to date model of a large advert fraud and residential proxy scheme referred to as BADBOX, portray an image of an interconnected cybercrime ecosystem.
This consists of SalesTracker Group, MoYu Group, Lemon Group, and LongTV, based on new findings from the HUMAN Satori Risk Intelligence and Analysis group, printed in collaboration with Google, Pattern Micro, Shadowserver, and different companions.
The “complicated and expansive fraud operation” has been codenamed BADBOX 2.0. It has been described as the most important botnet of contaminated linked TV (CTV) gadgets ever uncovered.
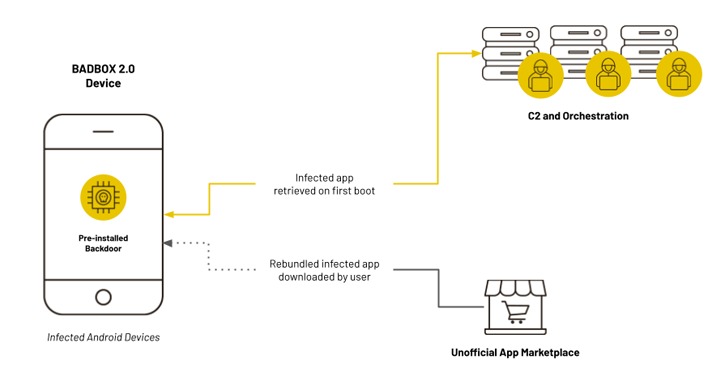
“BADBOX 2.0, like its predecessor, begins with backdoors on low-cost client gadgets that allow menace actors to load fraud modules remotely,” the corporate said. “These gadgets talk with command-and-control (C2) servers owned and operated by a sequence of distinct however cooperative menace actors.”
The menace actors are recognized to take advantage of a number of strategies, starting from {hardware} provide chain compromises to third-party marketplaces, to distribute what ostensibly look like benign purposes that include surreptitious “loader” performance to contaminate these gadgets and purposes with the backdoor.
The backdoor subsequently causes the contaminated gadgets to turn out to be half of a bigger botnet that is abused for programmatic advert fraud, click on fraud, and presents illicit residential proxy providers –
- Hidden advertisements and launching hidden WebViews to generate pretend advert income
- Navigation to low-quality domains and clicking on advertisements for monetary acquire
- Routing site visitors via compromised gadgets
- Utilizing the community for account takeover (ATO), pretend account creation, malware distribution, and DDoS assaults
As many as a million gadgets, primarily comprising cheap Android tablets, linked TV (CTV) packing containers, digital projectors, and automotive infotainment techniques, are estimated to have fallen prey to the BADBOX 2.0 scheme. All of the affected gadgets are manufactured in mainland China and shipped globally. A majority of the infections have been reported in Brazil (37.6%), america (18.2%), Mexico (6.3%), and Argentina (5.3%).
The operation has since been partially disrupted a second time in three months after an undisclosed variety of BADBOX 2.0 domains have been sinkhole in an try to chop off communications with the contaminated gadgets. Google, for its half, eliminated a set of 24 apps from the Play Retailer that distributed the malware. A portion of its infrastructure was previously taken down by the German authorities in December 2024.
“The contaminated gadgets are Android Open Supply Undertaking gadgets, not Android TV OS gadgets or Play Defend licensed Android gadgets,” Google mentioned. “If a tool is not Play Defend licensed, Google would not have a report of safety and compatibility check outcomes. Play Defend licensed Android gadgets endure in depth testing to make sure high quality and consumer security.”
The backdoor that types the core of the operation is predicated on an Android malware generally known as Triada. Codenamed BB2DOOR, it’s propagated in three alternative ways: A pre-installed element on the system, fetched from a distant server when booted for the primary time, and downloaded through greater than 200 trojanized variations of in style apps from third-party shops.
It is mentioned to be the handiwork of a menace cluster named MoYu Group, which advertises residential proxy providers constructed upon BADBOX 2.0-infected gadgets. Three different menace teams are accountable for overseeing different features of the scheme –
- SalesTracker Group, which is linked to the unique BADBOX operation in addition to a module that displays contaminated gadgets
- Lemon Group, which is linked to residential proxy providers based mostly on BADBOX and an advert fraud marketing campaign throughout a community of HTML5 (H5) sport web sites utilizing BADBOX 2.0
- LongTV, a Malaysian web and media firm whose two dozen apps are behind an advert fraud marketing campaign based mostly on an method generally known as “evil twin“
“These teams have been linked to at least one one other via shared infrastructure (frequent C2 servers) and historic and present enterprise ties,” HUMAN mentioned.
The most recent iteration represents a major evolution and adaptation, with the assaults additionally counting on contaminated apps from third-party app shops and a extra refined model of the malware that entails modifying legit Android libraries to arrange persistence.
Apparently, there’s some proof to counsel overlaps between BB2DOOR and Vo1d, one other malware that is recognized to particularly goal off-brand Android-based TV packing containers.
“The BADBOX 2.0 menace specifically is compelling in no small half due to the open-season nature of the operation,” the corporate added. “With the backdoor in place, contaminated gadgets might be instructed to hold out any cyber assault a menace actor developed.”
The event comes as Google removed over 180 Android apps spanning 56 million downloads for his or her involvement in a classy advert fraud scheme dubbed Vapor that leverages pretend Android apps to deploy infinite, intrusive full-screen interstitial video advertisements, per the IAS Risk Lab.
It additionally follows the invention of a new campaign that employs DeepSeek-themed decoy sites to trick unsuspecting customers into downloading an Android banking malware known as Octo.
Source link