The U.S. Cybersecurity and Infrastructure Safety Company (CISA) has added a high-severity safety flaw impacting NAKIVO Backup & Replication software program to its Identified Exploited Vulnerabilities (KEV) catalog, citing proof of energetic exploitation.
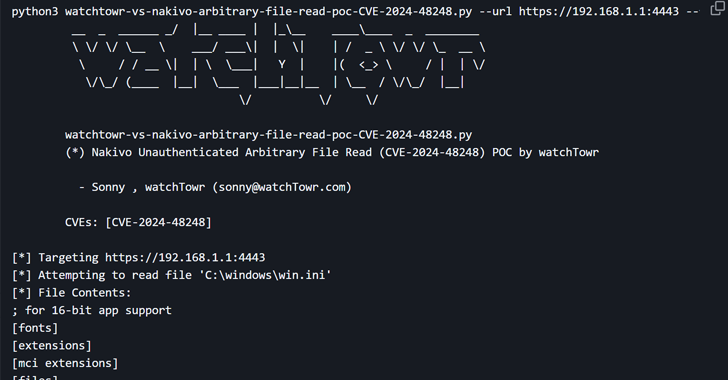
The vulnerability in query is CVE-2024-48248 (CVSS rating: 8.6), an absolute path traversal bug that would permit an unauthenticated attacker to learn recordsdata on the goal host, together with delicate ones comparable to “/and many others/shadow” by way of the endpoint “/c/router.” It impacts all variations of the software program previous to model 10.11.3.86570.
“NAKIVO Backup and Replication accommodates an absolute path traversal vulnerability that allows an attacker to learn arbitrary recordsdata,” CISA mentioned in an advisory.
Profitable exploitation of the shortcoming may permit an adversary to learn delicate information, together with configuration recordsdata, backups, and credentials, which may then act as a stepping stone for additional compromises.
There are at present no particulars on how the vulnerability is being exploited within the wild, however the growth comes after watchTowr Labs published a proof-of-concept (PoC) exploit in the direction of the top of final month. The difficulty has been addressed as of November 2024 with model v11.0.0.88174.
The cybersecurity agency additional famous that the unauthenticated arbitrary file learn vulnerability could possibly be weaponized to acquire all saved credentials utilized by the goal NAKIVO resolution and hosted on the database “product01.h2.db.”
Additionally added to the KEV catalog are two different flaws –
- CVE-2025-1316 (CVSS rating: 9.3) – Edimax IC-7100 IP digicam accommodates an OS command injection vulnerability as a consequence of improper enter sanitization that enables an attacker to attain distant code execution by way of specifically crafted requests (Unpatched as a result of system reaching end-of-life)
- CVE-2017-12637 (CVSS rating: 7.5) – SAP NetWeaver Software Server (AS) Java accommodates a directory traversal vulnerability in scheduler/ui/js/ffffffffbca41eb4/UIUtilJavaScriptJS that enables a distant attacker to learn arbitrary recordsdata by way of a .. (dot dot) within the question string
Final week, Akamai revealed that CVE-2025-1316 is being weaponized by dangerous actors to focus on cameras with default credentials as a way to deploy no less than two totally different Mirai botnet variants since Could 2024.
In gentle of energetic exploitation, Federal Civilian Govt Department (FCEB) companies are required to use the mandatory mitigations by April 9, 2025, to safe their networks.
Source link