Malware operations concentrating on holders of Ethereum, XRP, and Solana cryptocurrencies have been uncovered by cybersecurity researchers. The threat assaults Atomic and Exodus pockets house owners through the use of compromised software program packages put in by builders unaware of the malware contained within the code.
The malware, upon execution, is ready to ship cryptocurrency to thief-held addresses with no indication on the pockets proprietor.
How The Assault Works
Researchers say the assault begins when builders unwittingly embody hacked node package deal supervisor (NPM) packages of their tasks. One such package deal named “pdf-to-office” seems real on the floor however conceals malicious code inside.
The package deal searches computer systems for put in crypto wallets after which injects code that intercepts transactions. This permits criminals to steal cash with out the person’s consciousness or permission.
A number of Cryptocurrencies At Threat
Safety researchers have concluded that the malware can divert transactions on a number of of the world’s main cryptocurrencies. They embody Ethereum, USDT, XRP and Solana. The assault is what researchers determine as “an escalation within the ongoing concentrating on of cryptocurrency customers via software program provide chain assaults.”
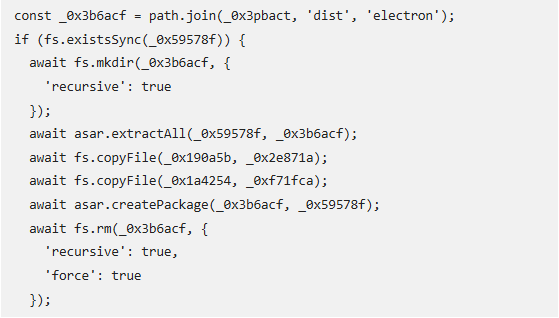
Technical Particulars Reveal Subtle Strategies
ReversingLabs found the marketing campaign by scanning for suspicious NPM packages. Their evaluation revealed a number of warning indicators similar to suspicious URL associations and code buildings matching well-known threats.
The assault employs subtle methods for evasion from safety instruments and is multi-stage in nature. The an infection begins when the malware package deal executes its code geared toward pockets software program on the goal’s machine. It particularly appears to be like for software recordsdata in among the predetermined paths earlier than injecting its malicious code.
No Visible Person Warning Indicators
In response to experiences, this malware’s impact could be catastrophic since transactions seem completely regular on the pockets interface. The code substitutes legitimate recipient addresses with attacker-controlled addresses via base64 encoding.
For example, when a person makes an attempt to ship ETH, the malware substitutes the recipient tackle with the attacker’s tackle, which is hid in encoded kind. Customers haven’t any visible clue that something is improper till they examine the blockchain file afterward and uncover their cash went to an sudden tackle.
The safety menace signifies elevated hurt to cryptocurrency house owners who may not bear in mind their transactions are compromised till funds go lacking. The modus operandi of the assault is proof of how hackers preserve developing with new strategies of pilfering digital belongings.
Cryptocurrency customers ought to be extraordinarily cautious when verifying all transaction addresses. Builders are additionally suggested to double-check the safety of any packages they set up on cryptocurrency-related tasks.
Featured picture from Enterprise Networking Planet, chart from TradingView
Source link

