The risk actor often called EncryptHub exploited a recently-patched safety vulnerability in Microsoft Home windows as a zero-day to ship a variety of malware households, together with backdoors and data stealers comparable to Rhadamanthys and StealC.
“On this assault, the risk actor manipulates .msc information and the Multilingual Consumer Interface Path (MUIPath) to obtain and execute malicious payload, keep persistence and steal delicate knowledge from contaminated techniques,” Pattern Micro researcher Aliakbar Zahravi said in an evaluation.
The vulnerability in query is CVE-2025-26633 (CVSS rating: 7.0), described by Microsoft as an improper neutralization vulnerability in Microsoft Administration Console (MMC) that would enable an attacker to bypass a safety characteristic domestically. It was fixed by the corporate earlier this month as a part of its Patch Tuesday replace.
Pattern Micro has given the exploit the moniker MSC EvilTwin, monitoring the suspected Russian exercise cluster below the identify Water Gamayun. The risk actor, just lately the subject of analyses by PRODAFT and Outpost24, can be referred to as LARVA-208.
CVE-2025-26633, at its core, leverages the Microsoft Administration Console framework (MMC) to execute a malicious Microsoft Console (.msc) file via a PowerShell loader known as MSC EvilTwin loader.
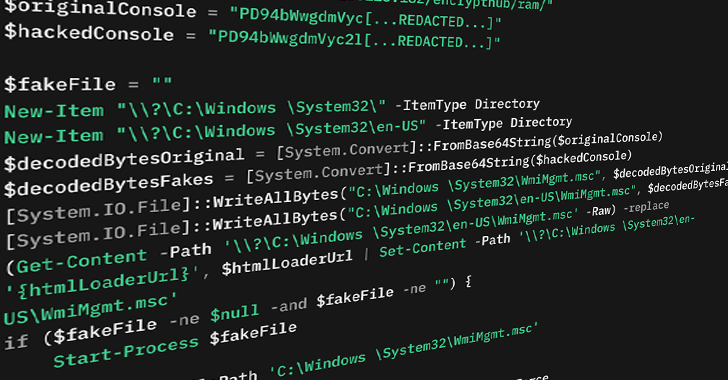
Particularly, it entails the loader creating two .msc information with the identical identify: One clear file and its rogue counterpart that’s dropped in the identical location however inside a listing named “en-US.” The thought is that when the previous is run, MMC inadvertently picks the malicious file as a substitute and executes it. That is completed by exploiting MMC’s Multilingual Consumer Interface Path (MUIPath) characteristic.
“By abusing the best way that mmc.exe makes use of MUIPath, the attacker can equip MUIPath en-US with a malicious .msc file, which trigger the mmc.exe load this malicious file as a substitute of the unique file and executed with out the sufferer’s information,” Zahravi defined.
EncryptHub has additionally been noticed adopting two different strategies to run malicious payload on an contaminated system utilizing .msc information –
- Utilizing the ExecuteShellCommand methodology of MMC to obtain and execute a next-stage payload on the sufferer’s machine, an method previously documented by Dutch cybersecurity firm Outflank in August 2024
- Utilizing mock trusted directories comparable to “C:Home windows System32” (word the house after Home windows) to bypass Consumer Account Management (UAC) and drop a malicious .msc file referred to as “WmiMgmt.msc”
Pattern Micro mentioned the assault chains probably start with victims downloading digitally-signed Microsoft installer (MSI) information impersonating respectable Chinese language software program like DingTalk or QQTalk, which is then used to fetch and execute the loader from a distant server. It is mentioned that the risk actor has been experimenting with these strategies since April 2024.
“This marketing campaign is below energetic growth; it employs a number of supply strategies and customized payloads designed to keep up persistence and steal delicate knowledge, then exfiltrate it to the attackers’ command-and-control (C&C) servers,” Zahravi mentioned.
Source link
 | Ethereum Foundation Blog
| Ethereum Foundation Blog