Your net browser is an ecosystem of its personal. It shops your passwords, search historical past, monetary particulars like bank card numbers, addresses and extra. Similar to how malicious apps and companies can compromise information in your cellphone or PC, malicious extensions can expose the information saved in your browser.
There are a ton of extensions on the market that do extra hurt than good. Actually, safety researchers have simply discovered a harmful new marketing campaign that’s going after browser extensions. Up to now, round 36 extensions have been compromised, placing over 2.6 million Chrome customers prone to having their shopping information and account credentials uncovered.
I’M GIVING AWAY THE LATEST & GREATEST AIRPODS PRO 2
Enter the giveaway by signing up for my free newsletter.

An individual utilizing a Chrome browser extension (Kurt “CyberGuy” Knutsson)
How hackers are focusing on browser extensions
Hackers are exploiting browser extensions as a gateway to steal delicate consumer information by quite a lot of strategies. These compromised extensions are exposing over 2.6 million customers to information publicity and credential theft, as reported by The Hacker News.
One widespread assault includes phishing campaigns focusing on the publishers of reliable extensions on platforms just like the Chrome Net Retailer. In these campaigns, attackers trick builders into granting permissions to malicious purposes, which then insert dangerous code into well-liked extensions. This code can steal cookies, entry tokens and different consumer information.
The primary firm to make clear the marketing campaign was cybersecurity agency Cyberhaven, considered one of whose workers have been focused by a phishing assault on December 24, permitting the menace actors to publish a malicious model of the extension.
As soon as these malicious extensions are revealed and move the Chrome Net Retailer’s safety evaluate, they’re made accessible to hundreds of thousands of customers, placing them prone to information theft. Attackers can use these extensions to exfiltrate shopping information, monitor consumer exercise and even bypass safety measures comparable to two-factor authentication.
In some instances, builders themselves might unknowingly embody data-gathering code as a part of a monetization software program improvement equipment, which stealthily exfiltrates detailed shopping information. This makes it tough to find out whether or not a compromise is the results of a hacking marketing campaign or an intentional inclusion by the developer.

Picture of a Chrome browser on a cellphone (Kurt “CyberGuy” Knutsson)
MASSIVE SECURITY FLAW PUTS MOST POPULAR BROWSERS AT RISK ON MAC
Take away these extensions out of your net browser
The browser extension safety platform Secure Annex has launched its personal investigation into this hacking marketing campaign. Up to now, it has uncovered over twenty further compromised extensions, that are listed beneath. If in case you have any of the compromised extensions listed in Safe Annex’s investigation put in in your browser, it’s important to take away them instantly to guard your information.
- AI Assistant – ChatGPT and Gemini for Chrome
- Bard AI Chat Extension
- GPT 4 Abstract with OpenAI
- Search Copilot AI Assistant for Chrome
- TinaMInd AI Assistant
- Wayin AI
- VPNCity
- Internxt VPN
- Vindoz Flex Video Recorder
- VidHelper Video Downloader
- Bookmark Favicon Changer
- Castorus
- Uvoice
- Reader Mode
- Parrot Talks
- Primus
- Tackker – on-line keylogger device
- AI Store Buddy
- Kind by Oldest
- Rewards Search Automator
- ChatGPT Assistant – Good Search
- Keyboard Historical past Recorder
- Electronic mail Hunter
- Visible Results for Google Meet
- Earny – As much as 20% Money Again
- Cyberhaven safety extension V3
- GraphQL Community Inspector
- Vidnoz Flex – Video recorder & Video share
- YesCaptcha assistant
- Proxy SwitchyOmega (V3)
- ChatGPT App
- Net Mirror
- Hello AI
Conserving these extensions put in is a critical threat since hackers can nonetheless entry your information even when the malicious model has been taken down from the Chrome Net Retailer. Safe Annex remains to be investigating and has shared a public Google Sheet with particulars in regards to the malicious extensions it has discovered to this point, like whether or not they’ve been up to date or eliminated. They’re additionally including new extensions to the record as they uncover them.
WORLD’S LARGEST STOLEN PASSWORD DATABASE UPLOADED TO CRIMINAL FORUM
take away an extension from Google Chrome
If in case you have put in one of many above-mentioned extensions in your browser, take away it as quickly as attainable. To take away an extension from Google Chrome, observe these steps:
- Open Chrome and click on the icon that appears like a bit of a puzzle. You will discover it within the top-right nook of the browser.
- You may see all of the lively extensions now. Click on the three dots icon subsequent to the extension you wish to take away and choose Take away from Chrome.
- Click on Take away to verify
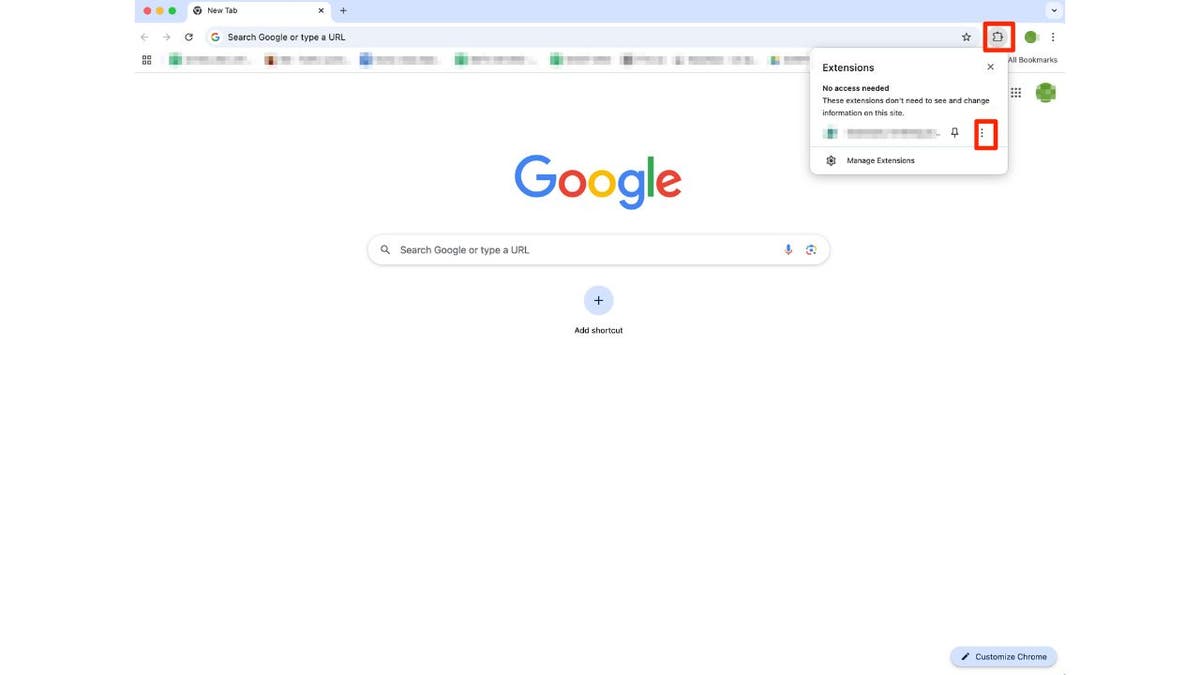
Steps to take away an extension from Google Chrome (Kurt “CyberGuy” Knutsson)
BEST ANTIVIRUS FOR MAC, PC, IPHONES AND ANDROIDS – CYBERGUY PICKS
7 methods to remain secure from malicious software program
1) Confirm emails and hyperlinks earlier than clicking: Many assaults start with phishing emails that impersonate trusted entities like Google Chrome Net Retailer Developer Help. These emails typically create a false sense of urgency, urging you to click on on malicious hyperlinks. All the time confirm the sender’s e mail handle and keep away from clicking on hyperlinks with out double-checking their authenticity. When doubtful, go on to the official web site somewhat than utilizing a supplied hyperlink.
2) Use robust antivirus software program: Having robust antivirus software program is a vital line of protection in opposition to malicious software program. These instruments can detect and block malicious code, even when it has been embedded in browser extensions. One of the simplest ways to safeguard your self from malicious hyperlinks that set up robust malware, doubtlessly accessing your non-public info, is to have antivirus software program put in on all of your gadgets. This safety also can provide you with a warning to phishing emails and ransomware scams, preserving your private info and digital belongings secure. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
3) Restrict extension permissions: Be cautious in regards to the permissions you grant to browser extensions. Many require entry to delicate information like shopping historical past, cookies or account info, however not all requests are vital. Evaluation what every extension asks for and deny permissions that appear extreme. If attainable, go for extensions with restricted entry to make sure your information stays protected.
4) Restrict the variety of extensions: Solely set up extensions which might be genuinely wanted and repeatedly evaluate and uninstall these not in use.
5) Maintain your browser up to date: All the time replace your browser to the newest model. Updates typically embody crucial safety patches that defend in opposition to vulnerabilities exploited by malicious software program. Utilizing an outdated browser will increase the chance of being focused by assaults that would have been prevented with a easy replace. Allow computerized updates to make sure you’re all the time protected. In case you are uncertain the best way to replace your browser, take a look at my detailed guide for Google Chrome.
6) Often audit your extensions: Conduct periodic critiques of put in extensions and take away any which might be pointless or pose potential safety dangers.
7) Report suspicious extensions: Should you encounter a suspicious extension, report it to the official browser extension market.
SUBSCRIBE TO KURT’S YOUTUBE CHANNEL FOR QUICK VIDEO TIPS ON HOW TO WORK ALL OF YOUR TECH DEVICES
Kurt’s key takeaway
Hackers are getting smarter, and browser extensions have turn into a brand new favourite goal for stealing delicate information. The invention of over 35 compromised Chrome extensions, placing 2.6 million customers in danger, is a wake-up name for everybody. Eradicating suspicious extensions is a vital step to guard your information. This additionally places Google’s Chrome Net Retailer evaluate course of beneath scrutiny, proving that even trusted platforms will be exploited.
How typically do you evaluate and take away unused or suspicious browser extensions? Tell us by writing us at Cyberguy.com/Contact.
For extra of my tech ideas and safety alerts, subscribe to my free CyberGuy Report Publication by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Observe Kurt on his social channels:
Solutions to essentially the most requested CyberGuy questions:
New from Kurt:
Copyright 2024 CyberGuy.com. All rights reserved.
Source link

