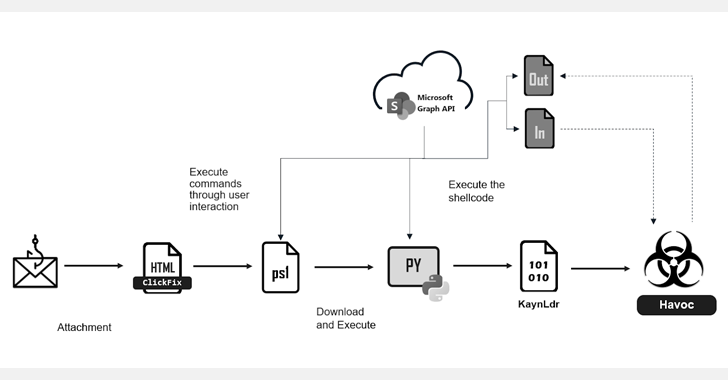
Cybersecurity researchers are calling consideration to a brand new phishing marketing campaign that employs the ClickFix method to ship an open-source command-and-control (C2) framework referred to as Havoc.
“The risk actor hides every malware stage behind a SharePoint website and makes use of a modified model of Havoc Demon along with the Microsoft Graph API to obscure C2 communications inside trusted, well-known providers,” Fortinet ForEGuard Labs said in a technical report shared with The Hacker Information.
The start line of the assault is a phishing electronic mail containing an HTML attachment (“Paperwork.html”) that, when opened, shows an error message, which makes use of the ClickFix technique to trick customers into copying and executing a malicious PowerShell command into their terminal or PowerShell, thereby triggering the next-stage.
The command is designed to obtain and execute a PowerShell script hosted on an adversary-controlled SharePoint server. The newly downloaded PowerShell checks if it is being run inside a sandboxed atmosphere earlier than continuing to obtain the Python interpreter (“pythonw.exe”), if it is not already current within the system.
The subsequent step includes fetching and executing a Python script from the identical SharePoint location that serves as a shellcode loader for KaynLdr, a reflective loader written in C and ASM that is able to launching an embedded DLL, on this the Havoc Demon agent on the contaminated host.
“The risk actor makes use of Havoc along with the MicrosoQ Graph API to hide C2 communication inside well-known providers,” Fortinet stated, including the framework helps options to collect info, carry out file operations, in addition to perform command and payload execution, token manipulation, and Kerberos assaults.
The event comes as Malwarebytes revealed that risk actors are continuing to exploit a known loophole in Google Adverts insurance policies to focus on PayPal prospects with bogus adverts served through advertiser accounts which will have been compromised.
The adverts search to trick victims trying to find help associated to account points or cost issues into calling a fraudulent quantity that probably ends with them handing over their private and monetary info.
“A weak spot inside Google’s insurance policies for landing pages (also called final URLs), permits anybody to impersonate widespread web sites as long as the touchdown web page and show URL (the webpage proven in an advert) share the identical area,” Jérôme Segura, senior director of analysis at Malwarebytes, said.
“Tech assist scammers are like vultures circling above the most well-liked Google search phrases, particularly in the case of any type of on-line help or customer support.”
Source link