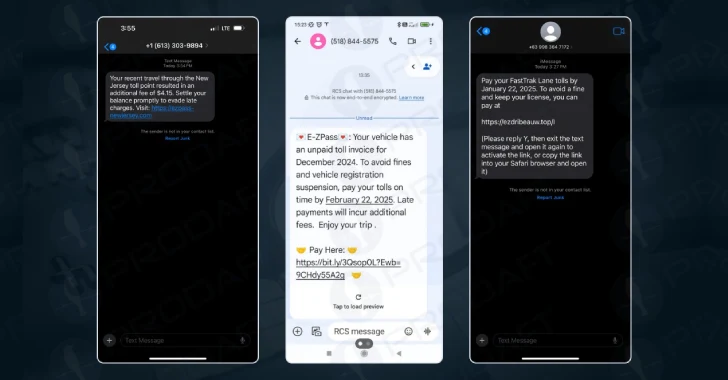
A brand new refined phishing-as-a-service (PhaaS) platform known as Lucid has focused 169 entities in 88 international locations utilizing smishing messages propagated through Apple iMessage and Wealthy Communication Companies (RCS) for Android.
Lucid’s distinctive promoting level lies in its weaponizing of reputable communication platforms to sidestep conventional SMS-based detection mechanisms.
“Its scalable, subscription-based mannequin permits cybercriminals to conduct large-scale phishing campaigns to reap bank card particulars for monetary fraud,” Swiss cybersecurity firm PRODAFT said in a technical report shared with The Hacker Information.
“Lucid leverages Apple iMessage and Android’s RCS know-how, bypassing conventional SMS spam filters and considerably rising supply and success charges.”
Lucid is assessed to be the work of a Chinese language-speaking hacking crew known as the XinXin group (aka Black Know-how), with the phishing campaigns primarily concentrating on Europe, the UK, and the USA with an intent to steal bank card knowledge and personally identifiable data (PII).
The menace actors behind the service, extra importantly, have developed different PhaaS platforms like Lighthouse and Darcula, the latter of which has been updated with capabilities to clone any model’s web site to create a phishing model. The developer of Lucid is a menace actor codenamed LARVA-242, who can be a key determine within the XinXin group.
All three PhaaS platforms share overlaps in templates, goal swimming pools, and techniques, alluding to a flourishing underground economic system the place Chinese language-speaking actors are leveraging Telegram to promote their warez on a subscription foundation for profit-driven motives.
Phishing campaigns counting on these companies have been discovered to impersonate postal companies, courier corporations, toll cost techniques, and tax refund companies, using convincing phishing templates to deceive victims into offering delicate data.
The big-scale actions are powered on the backend through iPhone gadget farms and cell gadget emulators working on Home windows techniques to ship a whole bunch of hundreds of rip-off messages containing bogus hyperlinks in a coordinated vogue. The cellphone numbers to be focused are acquired by way of varied strategies resembling knowledge breaches and cybercrime boards.
“For iMessage’s link-clicking restrictions, they employ ‘please reply with Y’ strategies to determine two-way communication,” PRODAFT defined. “For Google’s RCS filtering, they continuously rotate sending domains/numbers to keep away from sample recognition.”
“For iMessage, this includes creating short-term Apple IDs with impersonated show names, whereas RCS exploitation leverages provider implementation inconsistencies in sender verification.”
Apart from providing automation instruments that simplify the creation of customizable phishing web sites, the pages themselves incorporate superior anti-detection and evasion strategies like IP blocking, user-agent filtering, and time-limited single-use URLs.
Lucid additionally helps the flexibility to observe sufferer exercise and file each single interplay with the phishing hyperlinks in real-time through a panel, permitting its clients to extract the entered data. Bank card particulars submitted by victims are subjected to further verification steps. The panel is constructed utilizing the open-source Webman PHP framework.
“The Lucid PhaaS panel has revealed a extremely organized and interconnected ecosystem of phishing-as-a-service platforms operated by Chinese language-speaking menace actors, primarily below the XinXin group,” the corporate stated.
“The XinXin group develops and makes use of these instruments and earnings from promoting stolen bank card data whereas actively monitoring and supporting the event of comparable PhaaS companies.”
It is price noting that the findings from PRODAFT mirror that of Palo Alto Networks Unit 42, which recently known as out unspecified menace actors for using the area sample “com-” to register over 10,000 domains for propagating varied SMS phishing scams through Apple iMessage.
The event comes as Barracuda warned of a “large spike” in PhaaS assaults in early 2025 utilizing Tycoon 2FA, EvilProxy, and Sneaky 2FA, with every service accounting for 89%, 8%, and three% of all of the PhaaS incidents, respectively.
“Phishing emails are the gateway for a lot of assaults, from credential theft to monetary fraud, ransomware, and extra,” Barracuda safety researcher Deerendra Prasad said. “The platforms that energy phishing-as-a-service are more and more advanced and evasive, making phishing assaults each tougher for conventional safety instruments to detect and extra highly effective when it comes to the injury they’ll do.”
Source link