One of the vital energetic and infamous data-stealing ransomware teams, Maze, says it’s “formally closed.”
The announcement got here as a waffling assertion, riddled with spelling errors and printed on its web site on the darkish internet, which for the previous 12 months has printed huge troves of stolen inside paperwork and information from the businesses it focused, together with Cognizant, cybersecurity insurance coverage agency Chubb, pharmaceutical large ExecuPharm, Tesla and SpaceX elements provider Visser and protection contractor Kimchuk.
The place typical ransomware teams would infect a sufferer with file-encrypting malware and maintain the information for a ransom, Maze gained notoriety for first exfiltrating a sufferer’s knowledge and threatening to publish the stolen information until the ransom was paid.
It shortly became the preferred tactic of ransomware teams, which arrange web sites — usually on the darkish internet — to leak the information it stole if the sufferer refused to pay up.
Maze initially used exploit kits and spam campaigns to contaminate its victims, however later started utilizing identified safety vulnerabilities to particularly goal big-name firms. Maze was known to use weak digital non-public community (VPN) and distant desktop (RDP) servers to launch focused assaults in opposition to its sufferer’s community.
A number of the demanded ransoms reached into the tens of millions of {dollars}. Maze reportedly demanded $6 million from one Georgia-based wire and cable producer, and $15 million from one unnamed group after the group encrypted its community. However after COVID-19 was declared a pandemic in March, Maze — in addition to different ransomware teams — promised to not target hospitals and medical amenities.
However safety consultants aren’t celebrating simply but. In any case, ransomware gangs are nonetheless prison enterprises, lots of that are pushed by revenue.
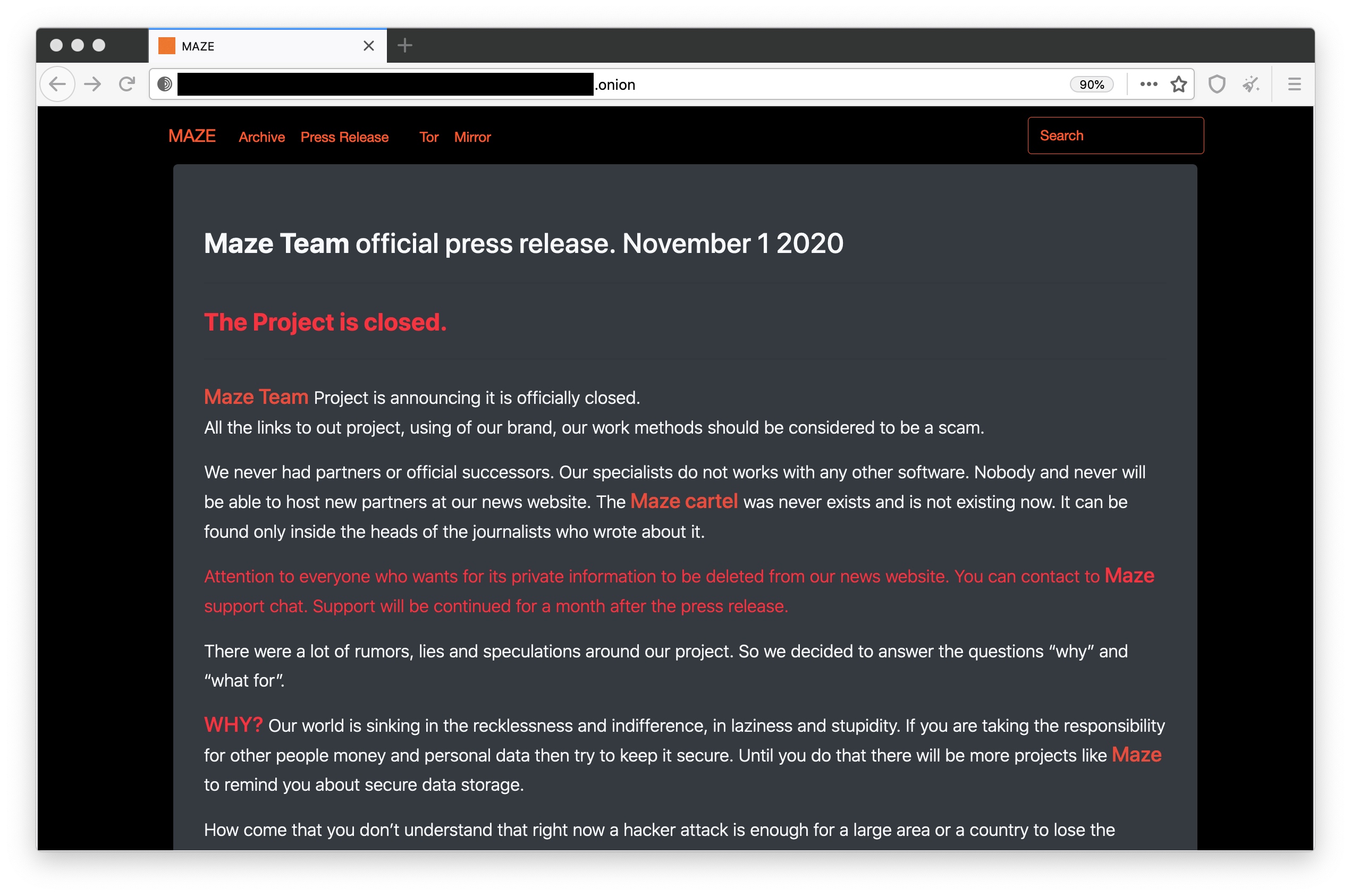
“Clearly, Maze’s claims needs to be taken with a really, very small pinch of salt,” stated Brett Callow, a ransomware knowledgeable and menace analyst at safety agency Emsisoft. “It’s actually attainable that the group feels they’ve made sufficient cash to have the ability to shut store and sail off into the sundown. Nevertheless, it’s additionally attainable — and possibly extra possible — that they’ve determined to rebrand.”
Callow stated the group’s obvious disbanding leaves open questions in regards to the Maze group’s connections and involvement with different teams. “As Maze was an affiliate operation, their companions in crime are unlikely to retire and can as an alternative merely align themselves with one other group,” he stated.
Maze denied that it was a “cartel” of ransomware teams in its assertion, however consultants disagree. Steve Ragan, a safety researcher at Akamai, stated Maze was identified to submit on its web site knowledge from different ransomware, like Ragnar Locker and the LockBit ransomware-for-hire.
“For them to fake now that there was no team-up or cartel is simply plain backwards. Clearly these teams had been working collectively on many ranges,” stated Ragan.
“The draw back to this, and the opposite vital ingredient, is that nothing will change, Ransomware remains to be going to be on the market,” stated Ragan. “Criminals are nonetheless focusing on open entry, uncovered RDP [remote desktop protocol] and VPN portals, and nonetheless sending malicious emails with malicious attachments within the hope of infecting unsuspecting victims on the web,” he stated.
Jeremy Kennelly at FireEye’s Mandiant menace intelligence unit stated that whereas the Maze model could also be useless, its operators are possible not gone for good.
“We assess with excessive confidence that lots of the people and teams that collaborated to allow the Maze ransomware service will possible proceed to have interaction in related operations — both working to help present ransomware providers or supporting novel operations sooner or later,” stated Kennelly.
As ransomware gets craftier, companies must start thinking creatively
Source link