A subgroup inside the notorious Russian state-sponsored hacking group often called Sandworm has been attributed to a multi-year preliminary entry operation dubbed BadPilot that stretched throughout the globe.
“This subgroup has performed globally various compromises of Web-facing infrastructure to allow Seashell Blizzard to persist on high-value targets and assist tailor-made community operations,” the Microsoft Menace Intelligence staff said in a brand new report shared with The Hacker Information forward of publication.
The geographical unfold of the preliminary entry subgroup’s targets embody the entire of North America, a number of international locations in Europe, in addition to others, together with Angola, Argentina, Australia, China, Egypt, India, Kazakhstan, Myanmar, Nigeria, Pakistan, Turkey, and Uzbekistan.
The event marks a big growth of the hacking group’s victimology footprint over the previous three years, which is in any other case identified to be concentrated round Jap Europe –
- 2022: Vitality, retail, training, consulting, and agriculture sectors in Ukraine
- 2023: Sectors in the US, Europe, Central Asia, and the Center East that offered materials assist to the battle in Ukraine or have been geopolitically important
- 2024: Entities in the US, Canada, Australia, and the UK
Sandworm is tracked by Microsoft beneath the moniker Seashell Blizzard (previously Iridium), and by the broader cybersecurity neighborhood beneath the names APT44, Blue Echidna, FROZENBARENTS, Gray Twister, Iron Viking, Razing Ursa, Telebots, UAC-0002, and Voodoo Bear. Energetic since at the least 2013, the group is assessed to be affiliated with Unit 74455 inside the Important Directorate of the Normal Workers of the Armed Forces of the Russian Federation (GRU).
The adversarial collective has been described by Google-owned Mandiant as an “extremely adaptive” and “operationally mature” risk actor that engages in espionage, assault, and affect operations. It additionally has a monitor file of mounting disruptive and destructive attacks towards Ukraine over the previous decade.
Campaigns mounted by Sandworm within the wake of the Russo-Ukrainian battle have leveraged information wipers (KillDisk aka HermeticWiper), pseudo-ransomware (Prestige aka PRESSTEA), and backdoors (Kapeka), along with malware households that permit the risk actors to take care of persistent remote access to contaminated hosts through DarkCrystal RAT (aka DCRat).
It has additionally been noticed counting on a wide range of Russian corporations and prison marketplaces to supply and maintain its offensive capabilities, highlighting a growing trend of cybercrime facilitating state-backed hacking.
“The group has used criminally sourced instruments and infrastructure as a supply of disposable capabilities that may be operationalized on brief discover with out fast hyperlinks to its previous operations,” the Google Menace Intelligence Group (GTIG) said in an evaluation.
“Since Russia’s full-scale invasion of Ukraine, APT44 has elevated its use of such tooling, together with malware resembling DarkCrystal RAT (DCRat), Warzone, and RADTHIEF (‘Rhadamanthys Stealer’), and bulletproof internet hosting infrastructure resembling that offered by the Russian-speaking actor ‘yalishanda,’ who advertises in cybercriminal underground communities.”
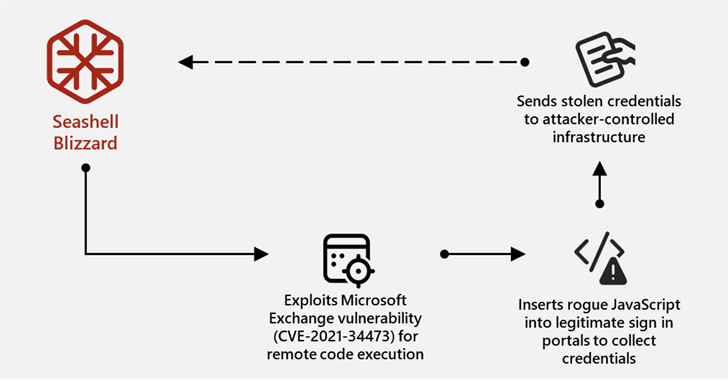
Microsoft stated the Sandworm subgroup has been operational since at the least late 2021, exploiting numerous identified safety flaws to acquire preliminary entry, adopted by a collection of post-exploitation actions geared toward amassing credentials, attaining command execution, and supporting lateral motion.
“Noticed operations following preliminary entry point out that this marketing campaign enabled Seashell Blizzard to acquire entry to international targets throughout delicate sectors together with vitality, oil and fuel, telecommunications, transport, arms manufacturing, along with worldwide governments,” the tech big famous.
“This subgroup has been enabled by a horizontally scalable functionality bolstered by revealed exploits that allowed Seashell Blizzard to find and compromise quite a few Web-facing techniques throughout a variety of geographical areas and sectors.”
Since early final 12 months, the sub-cluster is claimed to have weaponized vulnerabilities in ConnectWise ScreenConnect (CVE-2024-1709) and Fortinet FortiClient EMS (CVE-2023-48788) to infiltrate targets in the UK and the US.
Assaults carried out by the subgroup contain a mixture of each opportunistic “spray and pray” assaults and focused intrusions which might be designed to take care of indiscriminate entry and carry out follow-on actions to both develop community entry or get hold of confidential data.
It is believed that the big selection of compromises supply Seashell Blizzard a strategy to meet Kremlin’s ever-evolving strategic aims, allowing the hacking outfit to horizontally scale their operations throughout various sectors as new exploits are disclosed.
As many as eight completely different identified safety vulnerabilities have been exploited by the subgroup to this point,
A profitable foothold is succeeded by the risk actor establishing persistence by three completely different strategies –
- February 24, 2024 – current: Deployment of official distant entry software program resembling Atera Agent and Splashtop Distant Providers, in some circumstances abusing the entry to drop extra payloads for credential acquisition, information exfiltration, and different instruments for sustaining entry like OpenSSH and a bespoke utility dubbed ShadowLink that permits the compromised system to be accessible through the TOR anonymity community
- Late 2021 – current: Deployment of an internet shell named LocalOlive that permits for command-and-control and serves as a conduit for extra payloads, resembling tunneling utilities (e.g., Chisel, plink, and rsockstun)
- Late 2021 – 2024: Malicious modifications to Outlook Internet Entry (OWA) sign-in pages to inject JavaScript code that may harvest and exfiltrate credentials again to the risk actor in real-time, and alter DNS A-record configurations probably in an effort to intercept credentials from important authentication companies
“This subgroup, which is characterised inside the broader Seashell Blizzard group by its near-global attain, represents an growth in each the geographical concentrating on performed by Seashell Blizzard and the scope of its operations,” Microsoft stated.
“On the similar time, Seashell Blizzard’s far-reaching, opportunistic entry strategies probably supply Russia expansive alternatives for area of interest operations and actions that can proceed to be invaluable over the medium time period.”
The event comes as Dutch cybersecurity firm EclecticIQ linked the Sandworm group to a different marketing campaign that leverages pirated Microsoft Key Administration Service (KMS) activators and pretend Home windows updates to ship a brand new model of BACKORDER, a Go-based downloader that is liable for fetching and executing a second-stage payload from a distant server.
BACKORDER, per Mandiant, is normally delivered inside trojanized installer information and is hard-coded to execute the unique setup executable. The top purpose of the marketing campaign is to deliver DarkCrystal RAT.
“Ukraine’s heavy reliance on cracked software program, together with in authorities establishments, creates a significant assault floor,” safety researcher Arda Büyükkaya said. “Many customers, together with companies and important entities, have turned to pirated software from untrusted sources, giving adversaries like Sandworm (APT44) a main alternative to embed malware in broadly used applications.”
Additional infrastructure evaluation has uncovered a beforehand undocumented RDP backdoor codenamed Kalambur that is disguised as a Home windows replace, and which makes use of the TOR community for command-and-control, in addition to to deploy OpenSSH and allow distant entry through the Distant Desktop Protocol (RDP) on port 3389.
“By leveraging trojanized software program to infiltrate ICS environments, Sandworm (APT44) continues to reveal its strategic goal of destabilizing Ukraine’s important infrastructure in assist of Russian geopolitical ambitions,” Büyükkaya stated.
Source link