Cybersecurity researchers are alerting to a brand new marketing campaign that leverages internet injects to ship a brand new Apple macOS malware often known as FrigidStealer.
The exercise has been attributed to a beforehand undocumented menace actor often known as TA2727, with the knowledge stealers for different platforms similar to Home windows (Lumma Stealer or DeerStealer) and Android (Marcher).
TA2727 is a “menace actor that makes use of faux replace themed lures to distribute a wide range of malware payloads,” the Proofpoint Menace Analysis Staff said in a report shared with The Hacker Information.
It is one of many newly recognized menace exercise clusters alongside TA2726, which is assessed to be a malicious visitors distribution system (TDS) operator that facilitates visitors distribution for different menace actors to ship malware. The financially motivated menace actor is believed to be energetic since at the very least September 2022.
TA2726, per the enterprise safety agency, acts as a TDS for TA2727 and one other menace actor known as TA569, which is liable for the distribution of a JavaScript-based loader malware known as SocGholish (aka FakeUpdates) that usually masquerades as a browser replace on legitimate-but-compromised websites.
“TA2726 is financially motivated and works with different financially motivated actors similar to TA569 and TA2727,” the corporate famous. “That’s, this actor is probably liable for the online server or web site compromises that result in injects operated by different menace actors.”
Each TA569 and TA2727 share some similarities in that they’re distributed by way of web sites compromised with malicious JavaScript web site injects that mimic browser updates for internet browsers like Google Chrome or Microsoft Edge. The place TA2727 differs is the usage of assault chains that serve completely different payloads primarily based on recipients’ geography or machine.
Ought to a person go to an contaminated web site in France or the U.Ok. on a Home windows laptop, they’re prompted to obtain an MSI installer file that launches Hijack Loader (aka DOILoader), which, in flip, hundreds Lumma Stealer.
However, the identical faux replace redirect when visited from an Android machine results in the deployment of a banking trojan dubbed Marcher that has been detected in the wild for over a decade.
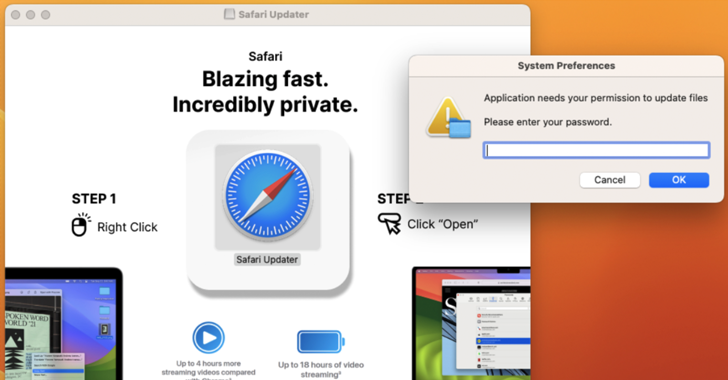
That is not all. As of January 2025, the marketing campaign has been up to date to focus on macOS customers residing outdoors of North America to a faux replace web page that downloaded a brand new data stealer codenamed FrigidStealer.
The FrigidStealer installer, like different macOS malware, requires customers to explicitly launch the unsigned app to bypass Gatekeeper protections, following which an embedded Mach-O executable is run to put in the malware.
“The executable was written in Go, and was ad-hoc signed,” Proofpoint stated. “The executable was constructed with the WailsIO venture, which renders content material within the person’s browser. This provides to the social engineering of the sufferer, implying that the Chrome or Safari installer was authentic.”
FrigidStealer is not any completely different from various stealer families aimed toward macOS programs. It leverages AppleScript to immediate the person to enter their system password, thereby giving it elevated privileges to reap information and all types of delicate data from internet browsers, Apple Notes, and cryptocurrency associated apps.
“Actors are utilizing internet compromises to ship malware focusing on each enterprise and shopper customers,” the corporate stated. “It’s affordable that such internet injects will ship malware custom-made to the recipient, together with Mac customers, that are nonetheless much less widespread in enterprise environments than Home windows.”
The event comes as Denwp Analysis’s Tonmoy Jitu disclosed particulars of one other totally undetectable macOS backdoor named Tiny FUD that leverages identify manipulation, dynamic hyperlink daemon (DYLD) injection, and command-and-control (C2) primarily based command execution.
It additionally follows the emergence of latest data stealer malware like Astral Stealer and Flesh Stealer, each of that are designed to gather delicate data, evade detection, and preserve persistence on compromised programs.
“Flesh Stealer is especially efficient in detecting digital machine (VM) environments,” Flashpoint said in a latest report. “It can keep away from executing on VMs to stop any potential forensics evaluation, showcasing an understanding of safety analysis practices.”
Source link