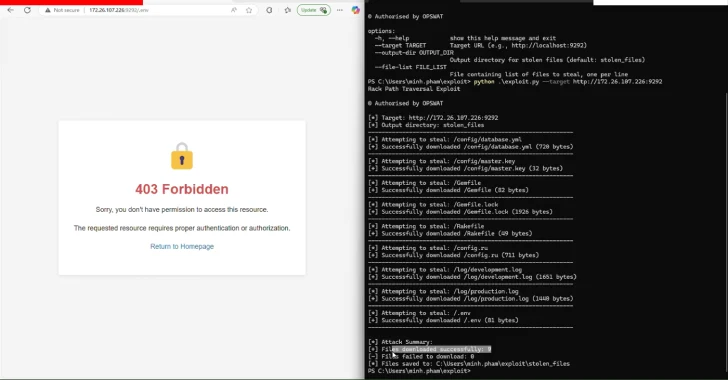
Cybersecurity researchers have disclosed three safety flaws within the Rack Ruby net server interface that, if efficiently exploited, may allow attackers to achieve unauthorized entry to recordsdata, inject malicious knowledge, and tamper with logs below sure circumstances.
The vulnerabilities, flagged by cybersecurity vendor OPSWAT, are listed under –
- CVE-2025-27610 (CVSS rating: 7.5) – A path traversal vulnerability that might be used to achieve entry to all recordsdata below the required root: listing, assuming an attacker can decide the paths to these recordsdata
- CVE-2025-27111 (CVSS rating: 6.9) – An improper neutralization of carriage return line feeds (CRLF) sequences and improper output neutralization for logs vulnerability that might be used to control log entries and deform log recordsdata
- CVE-2025-25184 (CVSS rating: 5.7) – An improper neutralization of carriage return line feeds (CRLF) sequences and improper output neutralization for logs vulnerability that might be used to control log entries and inject malicious knowledge
Profitable exploitation of the failings may allow an attacker to obscure assault traces, learn arbitrary recordsdata, and inject malicious code.
“Amongst these vulnerabilities, CVE-2025-27610 is especially extreme, because it may allow unauthenticated attackers to retrieve delicate data, together with configuration recordsdata, credentials, and confidential knowledge, thereby resulting in knowledge breaches,” OPSWAT stated in a report shared with The Hacker Information.
The shortcoming stems from the truth that Rack::Static, a middleware that is used to serve static content material like JavaScript, stylesheets, and pictures, doesn’t sanitize user-supplied paths earlier than serving recordsdata, resulting in a state of affairs the place an attacker can present a specifically crafted path to entry recordsdata outdoors of the static file listing.
“Particularly, when the :root parameter shouldn’t be explicitly outlined, Rack defaults this worth to the present working listing by assigning it the worth of Dir.pwd, implicitly designating it as the net root listing for the Rack software,” OPSWAT stated.
Because of this, if the :root choice is both undefined or misconfigured relative to the :urls choice, an unauthenticated attacker may weaponize CVE-2025-27610 via path traversal methods to entry delicate recordsdata outdoors the supposed net listing.
To mitigate the danger posed by the flaw, it is suggested to replace to the newest model. If rapid patching shouldn’t be an choice, it is advisable to take away utilization of Rack::Static, or be certain that root: factors at a listing path that solely incorporates recordsdata that must be accessed publicly.
Vital Flaw in Infodraw Media Relay Service
The disclosure comes as a crucial safety defect has been unearthed within the Infodraw Media Relay Service (MRS) that enables studying or deletion of arbitrary recordsdata by way of a path traversal vulnerability (CVE-2025-43928, CVSS rating: 9.8) within the username parameter within the login web page of the system.
Infodraw is an Israeli maker of cell video surveillance options which might be used to transmit audio, video, and GPS knowledge over telecommunications networks. In keeping with the company’s website, its units are utilized by regulation enforcement, non-public investigations, fleet administration, and public transport in lots of nations.
“A trivial Path Traversal vulnerability permits it to learn out any file from techniques for unauthenticated attackers,” safety researcher Tim Philipp Schäfers stated in an announcement shared with The Hacker Information. “Moreover an ‘Arbitrary File Deletion Vulnerability’ exists that enables attackers to delete any file from the system.”
The flaw, which allows login with a username like “../../../../,” impacts each Home windows and Linux variations of MRS. That stated, the flaw continues to stay unpatched. Weak techniques in Belgium and Luxembourg have been taken offline following accountable disclosure.
“Affected organizations are primarily suggested to take the applying offline instantly (since, regardless of early warnings, no producer patch is offered, and it’s thought-about doable that the vulnerability will likely be exploited by malicious actors within the close to future),” Philipp Schäfers said.
“If this isn’t doable, techniques must be additional protected with further measures (resembling utilizing a VPN or particular IP unlocking).”
Source link