Microsoft is looking consideration to an rising menace cluster it calls Storm-2372 that has been attributed to a brand new set of cyber assaults geared toward quite a lot of sectors since August 2024.
The assaults have focused authorities, non-governmental organizations (NGOs), data know-how (IT) companies and know-how, protection, telecommunications, well being, greater schooling, and power/oil and gasoline sectors in Europe, North America, Africa, and the Center East.
The menace actor, assessed with medium confidence to be aligned with Russian pursuits, victimology, and tradecraft, has been noticed concentrating on customers through messaging apps like WhatsApp, Sign, and Microsoft Groups by falsely claiming to be a outstanding individual related to the goal in an try and construct belief.
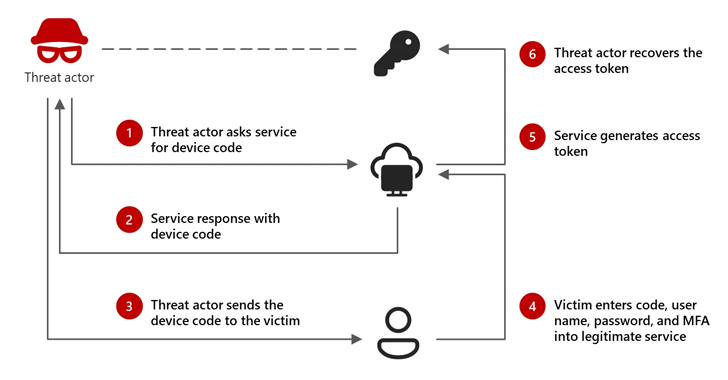
“The assaults use a particular phishing approach known as ‘system code phishing’ that tips customers to log into productiveness apps whereas Storm-2372 actors seize the knowledge from the log in (tokens) that they will use to then entry compromised accounts,” the Microsoft Menace Intelligence said in a brand new report.
The aim is to leverage the authentication codes obtained through the approach to entry goal accounts, and abuse that entry to pay money for delicate knowledge and allow persistent entry to the sufferer surroundings so long as the tokens stay legitimate.
The tech large stated the assault includes sending phishing emails that masquerade as Microsoft Groups assembly invites that, when clicked, urge the message recipients to authenticate utilizing a menace actor-generated system code, thereby permitting the adversary to hijack the authenticated session utilizing the legitimate entry token.
“In the course of the assault, the menace actor generates a official system code request and tips the goal into coming into it right into a official sign-in web page,” Microsoft defined. “This grants the actor entry and permits them to seize the authentication—entry and refresh—tokens which can be generated, then use these tokens to entry the goal’s accounts and knowledge.”
The phished authentication tokens can then be used to achieve entry to different companies that the consumer already has permissions to, similar to e-mail or cloud storage, with out the necessity for a password.
Microsoft stated the legitimate session is used to maneuver laterally inside the community by sending comparable phishing intra-organizational messages to different customers from the compromised account. Moreover, the Microsoft Graph service is used to look by messages of the breached account.
“The menace actor was utilizing key phrase looking to view messages containing phrases similar to username, password, admin, teamviewer, anydesk, credentials, secret, ministry, and gov,” Redmond stated, including the emails matching these filter standards have been then exfiltrated to the menace actor.
To mitigate the chance posed by such assaults, organizations are really helpful to block device code flow wherever potential, allow phishing-resistant multi-factor authentication (MFA), and comply with the precept of least privilege.
Source link