A brand new Android malware-as-a-service (MaaS) platform named SuperCard X can facilitate near-field communication (NFC) relay assaults, enabling cybercriminals to conduct fraudulent cashouts.
The lively marketing campaign is concentrating on prospects of banking establishments and card issuers in Italy with an purpose to compromise cost card knowledge, fraud prevention agency Cleafy mentioned in an evaluation. There may be proof to counsel that the service is promoted on Telegram channels.
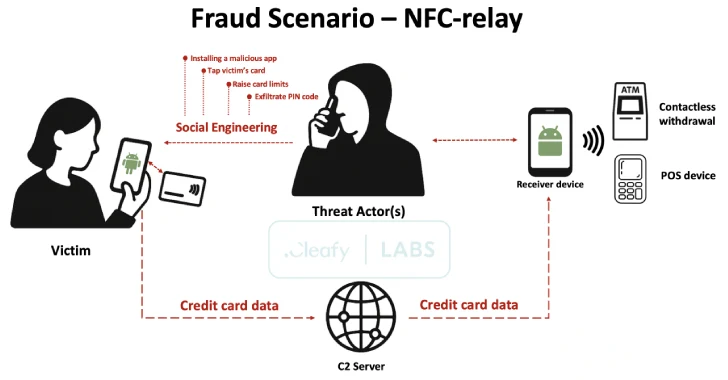
SuperCard X “employs a multi-stage strategy combining social engineering (through smishing and telephone calls), malicious utility set up, and NFC knowledge interception for extremely efficient fraud,” safety researchers Federico Valentini, Alessandro Strino, and Michele Roviello said.
The brand new Android malware, the work of a Chinese language-speaking risk actor, has been noticed being propagated through three totally different bogus apps, duping victims into putting in them through social engineering strategies like misleading SMS or WhatsApp messages –
- Verifica Carta (io.dxpay.remotenfc.supercard11)
- SuperCard X (io.dxpay.remotenfc.supercard)
- KingCard NFC (io.dxpay.remotenfc.supercard)
The messages impersonate financial institution safety alerts to induce a false sense of urgency by urging recipients to name a selected quantity to dispute the transaction.
The an infection chain then strikes to what’s known as a Phone-Oriented Assault Supply (TOAD), the place the risk actors manipulate victims to put in the app beneath the guise of safety software program by direct telephone conversations. The risk actors have additionally been discovered to make use of persuasive techniques to glean victims’ PINs and instruct them to take away any current card limits, thereby permitting them to empty the funds simply.
On the core of the operation is a beforehand undocumented NFC relay method that allows risk actors to fraudulently authorize point-of-sale (PoS) funds and Automated Teller Machine (ATM) withdrawals by intercepting and relaying NFC communications from contaminated gadgets.
To do that, the attackers urge the victims to convey their debit or bank card in shut bodily proximity to their cell gadget, which then permits the SuperCard X malware to stealthily seize the transmitted card particulars and relay them to an exterior server. The harvested card info is then utilized on a risk actor-controlled gadget to conduct unauthorized transactions.
The applying that is distributed to victims for capturing NFC card knowledge is known as a Reader. An identical app referred to as Tapper is put in on the risk actor’s gadget to obtain the cardboard info. Communication between the Reader and Tapper is carried out utilizing HTTP for command-and-control (C2) and requires cybercriminals to be logged in.
In consequence, risk actors are anticipated to create an account throughout the SuperCard X platform earlier than distributing the malicious apps, after which the victims are instructed to enter the login credentials offered to them in the course of the telephone name.
This step serves as a key cog within the total assault because it establishes the hyperlink between the sufferer’s contaminated gadget and the risk actor’s Tapper occasion, which then allows the cardboard knowledge to be relayed for subsequent money outs. The Tapper app can also be designed to emulate the sufferer’s card utilizing the stolen knowledge, thus fooling PoS terminals and ATMs into recognizing it as a respectable card.
The “Reader” malware artifacts recognized by Cleafy carry refined variations within the login display screen, indicating that they’re customized builds generated by affiliate actors to tailor the campaigns in response to their wants. As well as, SuperCard X makes use of mutual TLS (mTLS) to safe communication with its C2 infrastructure.
That risk actors might deceive unsuspecting customers into altering essential settings over telephone calls hasn’t gone unnoticed by Google, which is said to be working on a brand new Android characteristic that successfully blocks customers from putting in apps from unknown sources and granting permissions to accessibility companies.
Whereas there may be at the moment no proof that SuperCard X is distributed through the Google Play Retailer, customers are suggested to scrutinize app descriptions, permissions, and evaluations earlier than downloading them. It is also really useful to maintain Google Play Shield enabled to safeguard gadgets towards rising threats.
“This novel marketing campaign introduces a major monetary danger that extends past the traditional targets of banking establishments to have an effect on cost suppliers and bank card issuers immediately,” the researchers mentioned.
“The progressive mixture of malware and NFC relay empowers attackers to carry out fraudulent cash-outs with debit and bank cards. This methodology demonstrates excessive efficacy, particularly when concentrating on contactless ATM withdrawals.”
Source link