With US authorities businesses and lawmakers reportedly contemplating a ban on TP-Hyperlink’s merchandise in the USA, one may assume the corporate would rank excessive on the listing of networking distributors with probably the most vulnerabilities at present being exploited by cyberattackers.
Not by a protracted shot.
The Chinese language agency, whose merchandise are in style amongst shoppers and small companies, at present has two safety points gracing the Identified Exploited Vulnerabilities (KEV) listing curated by the Cybersecurity and Infrastructure Safety Company (CISA), in contrast with 74 for Cisco Methods, 23 for Ivanti, and 20 for D-Hyperlink.
But US authorities officers’ concern is much less about identified vulnerabilities, and extra about unknown dangers, together with its routers’ recognition in the USA — the place it accounts for about two-thirds of the market — and the diploma to which the corporate is beholden to China’s authorities.
Whereas no researcher has referred to as out a selected backdoor or zero-day vulnerability in TP-Hyperlink routers, proscribing merchandise from a rustic that may be a political and financial rival just isn’t unreasonable, says Thomas Tempo, CEO of prolonged Web of Issues (IoT) safety agency NetRise and a former head of cybersecurity for the US Division of Power.
“The worth to me [of a ban] is sort of extra round financial coverage worth than pure technical cybersecurity worth,” he says. “To me, there may be worth in saying you should not purchase this stuff due to X, Y, and Z causes [and to make it] harder for small companies, or whoever, to get their arms on units from these firms.”
TP-Hyperlink — Not a Vulnerability Stand-Out
In April 2024, one in all two TP-Hyperlink vulnerabilities attracted probably the most vulnerability scanning by risk actors, based on an analysis by cloud and application-security agency F5. The difficulty, a command injection vulnerability for TP-Hyperlink’s Archer AX21 router (CVE-2023-1389), permits an unauthenticated attacker to simply compromise a tool through a easy POST request.
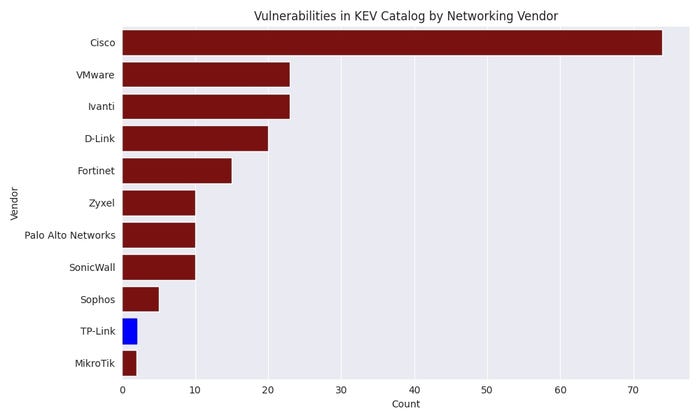
TP-Hyperlink ranks low on the listing of networking distributors with identified exploited vulnerabilities. Supply: Creator from CISA knowledge
In one other incident, safety agency Test Level Software program Applied sciences found that TP-Hyperlink units have been additionally compromised with an implant often called Camaro Dragon. The implanted elements have been found in modified TP-Hyperlink firmware photos, and never the unique software program shipped by the corporate, says Itay Cohen, analysis lead at Test Level Analysis.
But Cohen stresses that the implants have been written in a firmware-agnostic method and never particular to any specific product or vendor.
“It’s price noting that this sort of assault just isn’t aimed particularly at delicate networks, however moderately at common residential and residential networks,” he says. “Subsequently, infecting a house router doesn’t essentially imply that the house owner was a selected goal, however moderately that their gadget was merely a means to an end for the attackers.”
The risk posed by such vulnerabilities and implants are actual, however the knowledge from the KEV catalog reveals that different producers are simply as prone to have their vulnerabilities exploited — and there are extra of them. The lesson is that vulnerabilities in embedded units aren’t distinctive to anybody producer or nation of origin, says Sonu Shankar, chief product officer at Phosphorus Cybersecurity, an prolonged IoT cybersecurity supplier.
“Nation-state actors incessantly exploit weaknesses in units from firms worldwide, together with these bought by American producers,” he says. “Gadgets missing primary safety hygiene — comparable to the usage of sturdy passwords, well timed firmware patching, or correct configurations — can turn out to be simple targets for cyberattacks.”
TP-Hyperlink careworn this truth in an announcement despatched to Darkish Studying.
“Many manufacturers of client electronics are focused by hackers, and we help authorities efforts to carry all producers to the identical commonplace,” an organization spokesperson stated. “We welcome alternatives to interact with the federal authorities to reveal that our safety practices are absolutely in keeping with business safety requirements, and to reveal our ongoing dedication to the American market, American shoppers, and addressing US nationwide safety dangers.”
China’s Authorities Oversight Is Pervasive
However these assertions could also be minimizing the affect of the Chinese language authorities on the corporate’s operations: Most Western firms don’t perceive the diploma to which Chinese language officers monitor China’s enterprise sectors — and cybersecurity corporations — as a part of presidency coverage and nationwide technique, NetRise’s Tempo says.
“It is a completely totally different enterprise tradition,” he says. “There’s a member of the PRC in each firm — that is not even like an opinion, it is simply how it’s. And for those who assume they don’t seem to be there to exert their affect, you then’re simply an unbelievably naive individual, as a result of that is precisely what they do, [including] for the needs of intelligence gathering.”
Risk intelligence analysts have flagged the Chinese language authorities nationwide technique paperwork and proof displaying their growing efforts to compromise rival nations’ infrastructure — such because the assaults by Volt Typhoon and Salt Typhoon.
“In recent times we see Chinese language risk actors’ growing curiosity in compromising edge units, aiming to each construct resilient and extra nameless C2 infrastructures, and to achieve a foothold in sure focused networks,” Test Level acknowledged in its evaluation, however added that the “discovery of the firmware-agnostic nature of the implanted elements signifies that a variety of units and distributors could also be in danger.”
China’s networking merchandise aren’t alone in being focused by the US authorities, which additionally banned the products of antivirus firm Kaspersky due to nationwide safety issues, on condition that it is a Russian firm.
The World Cyber Actuality of Residence Routers: Purchaser Beware
Firms and shoppers ought to do their due diligence, hold their units updated with the most recent safety patches, and think about whether or not the producer of their vital {hardware} could have secondary motives, says Phosphorus Cybersecurity’s Shankar.
“The overwhelming majority of profitable assaults on IoT are enabled by preventable points like static, unchanged default passwords, or unpatched firmware, leaving methods uncovered,” he says. “For enterprise operators and client end-users, the important thing takeaway is evident: adopting primary safety hygiene is a vital protection towards each opportunistic and complex assaults. Don’t go away the entrance door open.”
For firms nervous in regards to the origin of their networking units or the safety their provide chain, discovering a trusted third occasion to handle the units is an inexpensive possibility. In actuality, although, virtually each gadget must be monitored and never trusted, says NetRise’s Tempo.
“It is a loopy world that exists relating to gadget safety,” he says. “You are accepting this gadget that you recognize nothing about — and that you simply actually cannot know something about — in contrast to Home windows [or another operating system] … the place you may also set up three brokers and a firewall in entrance of it to mitigate the chance of the software program.”
Source link

